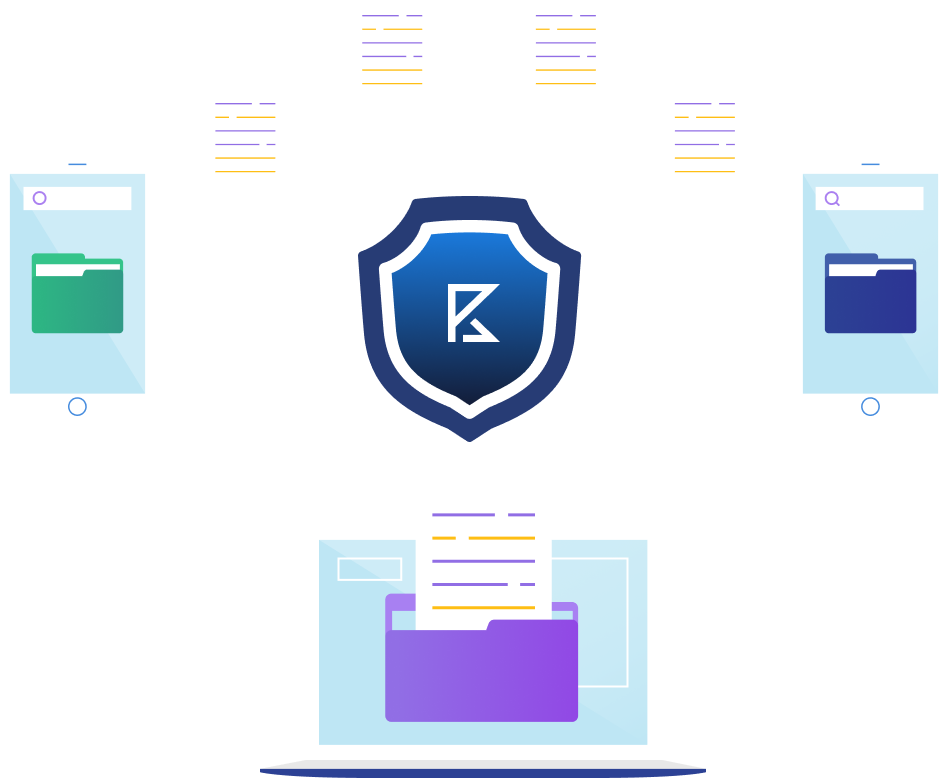
We've spent over six years developing a PQC end-to-end encryption protocol that truly encrypts your data, Hotmail, Outlook, Live, and Gmail. We add encryption to your existing email. You create the encryption key on your device (browser), so no one can access your key or your data. Not even us at KeyPact. Therefore, we can never hand over the key or lose it through a (server) hack.
We have over 50 years of combined experience in developing complex and secure protocols. In recent years, we've been developing the KeyPact Protection Protocol. Thanks to the KPP, you can confidently store data and email anywhere in the world in the cloud. We encrypt email from all Outlook versions, including Gmail. We also have our own email client. All email is truly end-to-end encrypted. Contact us to learn how we can help you.
Every time you save something, a new key is created to encrypt the file, email, photo, or video. So everything gets its own encryption key! While others store the key on a server, at KeyPact, the encryption key stays on your computer or phone. No one has access to it, not even us at KeyPact.


%201.png)